Outbound NAT¶
Outbound NAT, also known as Source NAT, controls how pfSense® software will translate the source address and ports of traffic leaving an interface. To configure Outbound NAT, navigate to Firewall > NAT, on the Outbound tab.
There are four possible Modes for Outbound NAT:
- Automatic Outbound NAT
The default option, which automatically performs NAT from internal interfaces, such as LAN, to external interfaces, such as WAN.
- Hybrid Outbound NAT
Utilizes manual rules while also using automatic rules for traffic not matched by manually entered rules. This mode is the most flexible and easy to use for administrators who need a little extra control but do not want to manage the entire list manually.
- Manual Outbound NAT
Only honors the manually entered rules, and nothing more. Offers the most control, but can be tough to manage and any changes made to internal interfaces or WANs must be accounted for in the rules by hand. If the list is empty when switching from automatic to manual, the list is populated with rules equivalent to the automatically generated set.
- Disable Outbound NAT
Disables all outbound NAT. Useful if the firewall contains only routable addresses (e.g. public IP addresses) on all LANs and WANs.
When changing the Mode value, click the Save button to store the new value.
In networks with a single public IP address per WAN, there is usually no reason to enable manual outbound NAT. If some manual control is necessary, hybrid mode is the best choice. In environments with multiple public IP addresses and complex NAT requirements, manual outbound NAT offers more fine-grained control over all aspects of translation.
For environments using High Availability with CARP, it is important to NAT outbound traffic to a CARP VIP address, as discussed in High Availability. This can be accomplished in either hybrid or manual mode.
As with other rules in pfSense, outbound NAT rules are considered from the top of the list down, and the first match is used. Even if rules are present in the Outbound NAT screen, they will not be honored unless the Mode is set to Hybrid Outbound NAT or Manual Outbound NAT.
Note
Outbound NAT only controls what happens to traffic as it leaves an interface. It does not control the interface though which traffic will exit the firewall. That is handled by the routing table (Static Routes) or policy routing (Policy routing).
Default Outbound NAT Rules¶
When set to the default Automatic Outbound NAT mode, pfSense maintains a set of NAT rules to translate traffic leaving any internal network to the IP address of the WAN interface which the traffic leaves. Static route networks and remote access VPN networks are also included in the automatic NAT rules.
When outbound NAT is configured for Automatic or Hybrid modes, the automatic rules are presented in the lower section of the screen labeled Automatic Rules.
If the Outbound NAT rule list is empty, switching to Manual Outbound NAT and saving will generate a full set of rules equivalent to the automatic rules.
Static Port¶
By default, pfSense software rewrites the source port on all outgoing
connections except for UDP port 500 (IKE for IPsec VPN traffic). Some
operating systems do a poor job of source port randomization, if they do it at
all. This makes IP address spoofing easier and makes it possible to fingerprint
hosts behind the firewall from their outbound traffic. Rewriting the source port
eliminates these potential (but unlikely) security vulnerabilities. Outbound NAT
rules, including the automatic rules, will show 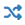 in the Static
Port column on rules set to randomize the source port.
in the Static
Port column on rules set to randomize the source port.
Source port randomization breaks some rare applications. The default Automatic
Outbound NAT ruleset disables source port randomization for UDP 500 because
it will almost always be broken by rewriting the source port. Outbound NAT rules
which preserve the original source port are called Static Port rules and
have  on the rule in the Static Port column. All other traffic has
the source port rewritten by default.
on the rule in the Static Port column. All other traffic has
the source port rewritten by default.
Other protocols, such as those used by game consoles, may not work properly when the source port is rewritten. To disable this functionality, use the Static Port option.
To add a rule for a device which requires static source ports:
Navigate to Firewall > NAT, Outbound tab
Select Hybrid Outbound NAT rule generation
Click Save
Click
 to add a new NAT rule to the top of the list
to add a new NAT rule to the top of the listConfigure the rule to match the traffic that requires static port, such as a source address of a PBX or a game console (See Working with Manual Outbound NAT Rules below)
Check Static Port in the Translation section of the page
Click Save
Click Apply Changes
After making that change, the source port on outgoing traffic matching the rule will be preserved. The best practice is to use strict rules when utilizing static port to avoid any potential conflict if two local hosts use the same source port to talk to the same remote server and port using the same external IP address.
Disabling Outbound NAT¶
If public IP addresses are used on local interfaces, and thus NAT is not required to pass traffic through the firewall, disable NAT for the routable subnet. This can be achieved in several ways:
If NAT is not required for any interface, set the outbound NAT mode to Disable
Using Hybrid Outbound NAT, a rule set with Do not NAT can disable NAT for matching traffic
Using Manual Outbound NAT, delete (or do not create) any NAT rules matching the routable subnets
In any of the above cases, outbound NAT will no longer be active for those source IP addresses and pfSense software will then route public IP addresses without translation.
Working with Manual Outbound NAT Rules¶
Outbound NAT rules are very flexible and are capable of translating traffic in many ways.
The NAT rules are shown in a single page and the Interface column is a source of confusion for some; As traffic leaves an interface, only the outbound NAT rules set for that specific Interface are consulted.
Click  from the Outbound NAT page to add a rule to the top of
the list. Click
from the Outbound NAT page to add a rule to the top of
the list. Click  to add a rule to the bottom. Place specific rules
at the top, and more general rules at the bottom. The rules are processed by the
firewall starting at the top of the list and working down, and the first rule to
match is used. Rules may be reordered to match in the desired way.
to add a rule to the bottom. Place specific rules
at the top, and more general rules at the bottom. The rules are processed by the
firewall starting at the top of the list and working down, and the first rule to
match is used. Rules may be reordered to match in the desired way.
The options for each Outbound NAT rule are:
- Disabled
Toggles whether or not this rule is active.
- Do not NAT
Checking this option causes packets matching the rule to not have NAT applied as they leave. This is necessary if the traffic would otherwise match a NAT rule, but must not have NAT applied. One common use for this is to add a rule exception so that the firewall IP addresses do not get NAT applied, especially in the case of CARP, where such NAT would break Internet communication from a secondary node while it is in backup mode.
- Interface
The interface where this NAT rule will apply when traffic is leaving via this interface. Typically this is WAN or an OPT WAN, but in some special cases it could be LAN or another internal interface.
- Protocol
In most cases, Outbound NAT will apply to any protocol, but occasionally it is necessary to restrict the protocol upon which the NAT will act. For example, to only perform static port NAT for UDP traffic from a PBX.
- Source
The Source is the local network which will have its address translated as it leaves the selected Interface. This is typically a LAN, DMZ, or VPN subnet. The Source Port is nearly always left blank to match all ports. This field supports the use of aliases if the Type is set to Network or Alias.
Note
Avoid using a source address of any as that will also match traffic from the firewall itself. This will cause problems with gateway monitoring and other firewall-initiated traffic.
- Destination
In most cases, the Destination remains set to any so that traffic going anywhere out of this Interface will be translated, but the Destination can be restricted as needed. For example, to translate in a certain way when going to a specific destination, such as only doing static port NAT to SIP trunk addresses. This field supports the use of aliases if the Type is set to Network or Alias.
- Translation
The Address field inside of the Translation section controls what happens to the source address of traffic matching this rule. Most commonly, this is set to the Interface Address so the traffic is translated to the IP address of Interface, e.g. the WAN IP address. The Address drop-down also contains all defined Virtual IP addresses and subnets, and Network or Alias to manually enter a subnet for translation.
Note
An alias containing subnets cannot be used for translation. Only host aliases or a single manually entered subnet may be used.
Using a host alias or manually entered subnet, an outbound NAT rule can translate to a pool of addresses. This can help in large NAT deployments or in areas where static port is required for several clients. When translating to a host alias or subnet, a Pool Options drop-down is available with several options. Only Round Robin types work with host aliases. Any type may be used with a subnet.
- Default
Does not define any specific algorithm for selecting a translation address from the pool.
- Round Robin
Loops through each potential translation address in the alias or subnet in turn.
- Round Robin with Sticky Address
Works the same as Round Robin but maintains the same translation address for a given source address as long as states from the source host exist.
- Random
Selects a translation address for use from the subnet at random.
- Random with Sticky Address
Selects an address at random, but maintains the same translation address for a given source address as long as states from the source host exist.
- Source Hash
Uses a hash of the source address to determine the translation address, ensuring that the translated address is always the same for a given source IP address.
- Bitmask
Applies the subnet mask and keeps the last portion identical. For example if the source address is
10.10.10.50and the translation subnet is192.2.0.0/24, the rule will change the address to192.2.0.50. This works similarly to 1:1 NAT but only in the outbound direction.
- Port
Specifies a specific source port for translation. This is almost always left blank, but could be required if the client selects a random source port but the server requires a specific source port.
- Static Port
Causes the original source port of the client traffic to be maintained after the source IP address has been translated. Some protocols require this, like IPsec without NAT-T, and some protocols behave better with this, such as SIP and RTP. Checking this option disables the Port entry box.
- No XML-RPC Sync
This option is only relevant if an HA Cluster configuration is in use, and should be skipped otherwise. When using an HA cluster with configuration synchronization, checking this box will prevent the rule from being synchronized to the other members of a cluster (see High Availability). Typically all rules should synchronize, however. This option is only effective on primary nodes, it does not prevent a rule from being overwritten on secondary nodes.
- Description
An optional text reference to explain the purpose of this rule.
These rules can accommodate most any NAT scenario, large or small.
Tracking Changes to Outbound NAT Rules¶
As mentioned in Figure Firewall Rule Time Stamps for firewall rules, a timestamp is added to an outbound NAT entry indicating when it was created or last edited. This timestamp shows which user created the rule, and the last person to edit the rule. When switching from Automatic Outbound NAT mode to Manual Outbound NAT mode, the created rules are marked as being created by that process.